7+ HIPAA Security Risk Analysis Examples to Download
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule requires that covered entities and its business associates conduct a risk assessment of their healthcare organization. A risk assessment helps your organization ensure it is compliant with HIPAA’s administrative, physical, and technical safeguards. A risk assessment also helps reveal areas where your organization’s protected health information could be at risk.
- 9+ HIPAA Confidentiality Agreement Examples – PDF
- 11+ Mutual Confidentiality Agreement Examples – PDF, Word
The HIPAA was developed by the National Institute of Standards and Technology (NIST) and is intended to help organizations better understand the requirements of the HIPAA Security Rule, implement those requirements, and assess those implementations in their operational environment. Target uses include, but are not limited to, HIPAA covered entities, business associates, and other organizations such as those providing HIPAA Security Rule implementation, assessment, and compliance services.
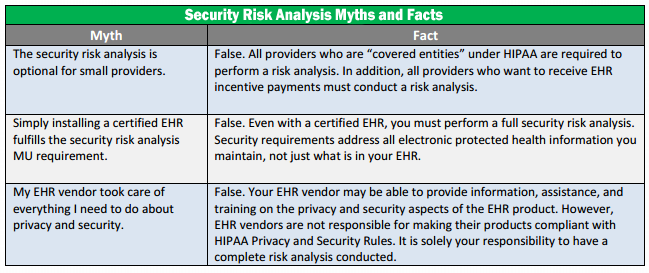
HIPAA Security Risk Analysis Myths
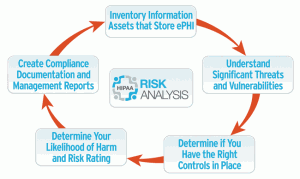
What’s in a HIPAA Risk Analysis?
The Department of Health and Human Services requires all organizations handling protected health information (PHI), including HIPAA hosting providers, to conduct a risk analysis as the first step toward implementing safeguards specified in the HIPAA Security Rule, and ultimately achieving HIPAA compliance.
But what does a risk analysis entail, and what do you absolutely have to include in your report? The HHS Security Standards Guide outline nine mandatory components of a risk analysis that healthcare organizations and healthcare-related organizations that store or transmit electronic protected health information must include in their document.
The Scope of the Analysis
Any potential risks and vulnerabilities to the privacy, availability, and integrity of the PHI, such as portable media, desktops, and networks. Network security between multiple locations is also important to include in the scope of the analysis and may include aspects of your HIPAA hosting terms with a third party or business associate.
Data Collection
Where does the PHI go? Locate where the data is being stored, received, maintained or transmitted. Again, if you’re hosting health information at a HIPAA compliant data center, you’ll need to contact your hosting provider to document where and how your data is stored.
Identify and Document Potential Threats and Vulnerabilities
Identify and document any anticipated threats to sensitive data, and any vulnerabilities that may lead to leaking of PHI. Anticipating potential HIPAA violations can help your organization quickly and effectively reach a resolution.
Assess Current Security Measure
What kind of security measures are you taking to protect your data? From a technical perspective, this might include any encryption, two-factor authentication, and other security methods put in place by your HIPAA hosting provider.
Determine the Likelihood of Threat Occurrence
Take account of the probability of potential risks to PHI—in combination with #3 Potential Threats and Vulnerabilities, this assessment allows for estimates on the likelihood of ePHI breaches.
Determine the Potential Impact of Threat Occurrence
By using either qualitative or quantitative methods, assess the maximum impact of a data threat to your organization. How many people could be affected? What extent of private data could be exposed—just medical records, or both health information and billing information combined?
Determine the Level of Risk
Take the average of the assigned likelihood and impact levels to determine the level of risk. Documented risk levels should be accompanied by a list of corrective actions that would be performed to mitigate risk.
Finalize Documentation
Write everything up in an organized document. There is no specified format for this, but it is required to have the analysis in writing.
Periodic Review and Updates to the Risk Assessment
It is important to conduct a risk analysis on a regular basis. While the Security Rule doesn’t set a required timeline, it is recommended for organizations to conduct another risk analysis whenever the company implements or plans to adopt a new technology or business operation. This could include switching your data storage methods from managed servers to cloud computing, or any ownership or key staff turnover.
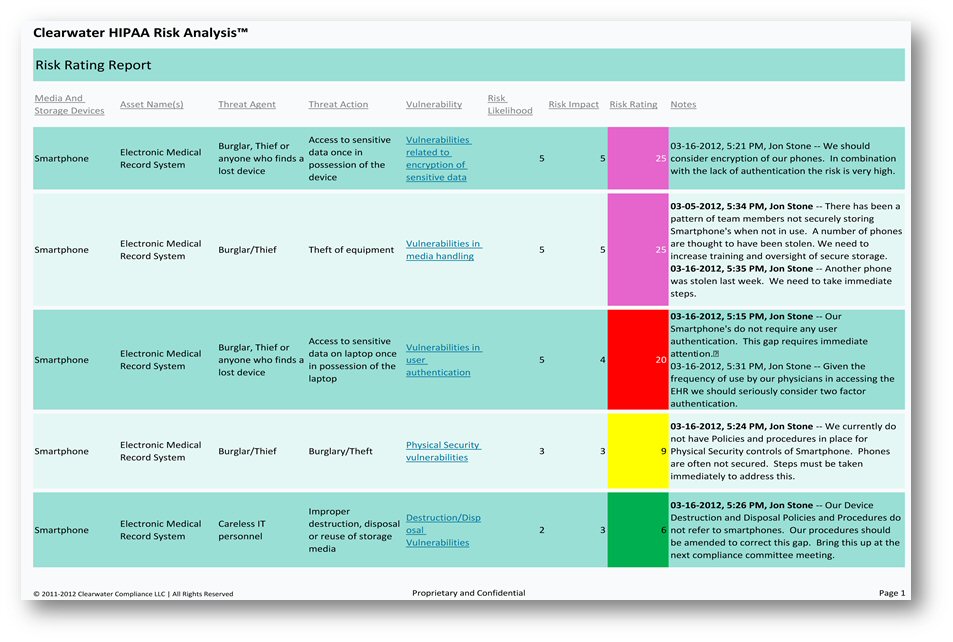
Clearwater HIPAA Risk Analysis
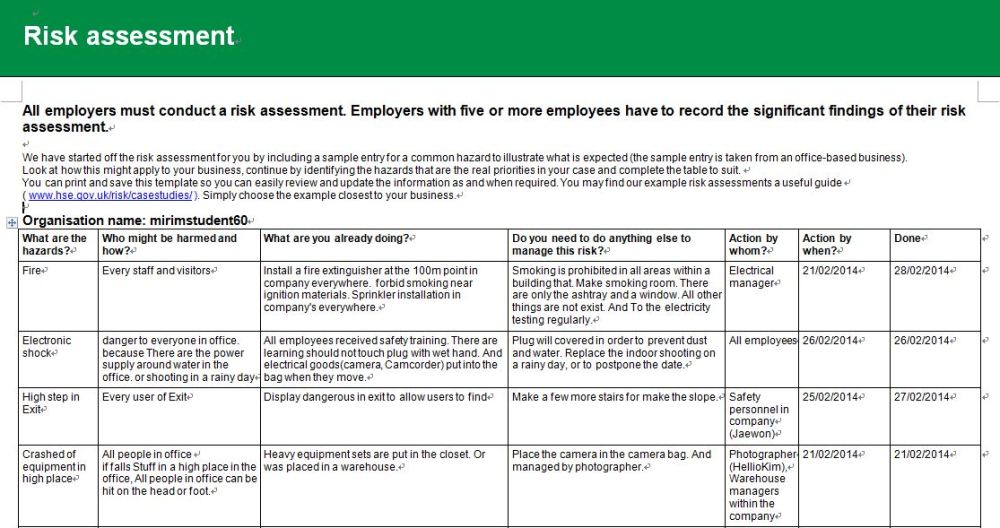
HIPAA Risk Assessment Example
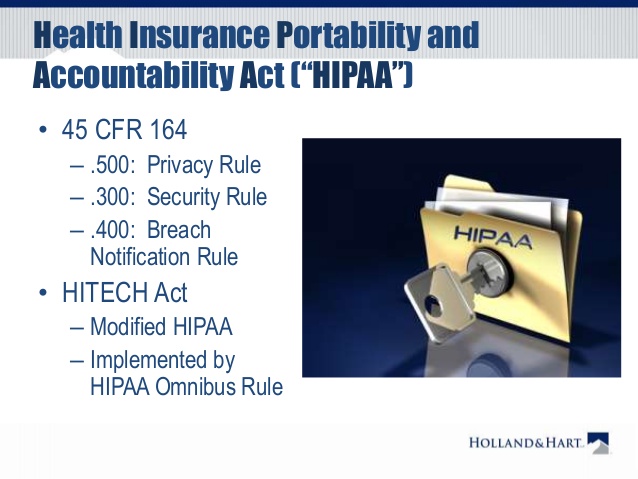
Health Insurance Portability and Accountability Act or HIPAA
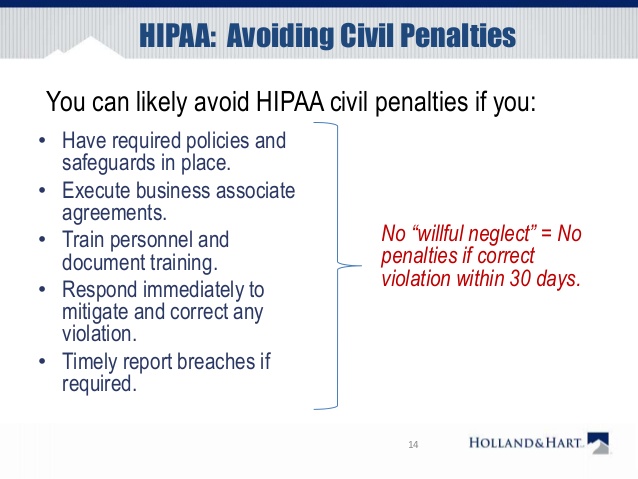
HIPAA: Avoiding Civil Penalties
Top Reasons to Conduct a Thorough HIPAA Security Risk Analysis
As most healthcare providers know, HIPAA requires that covered entities or business associates conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.
Providers who receive Meaningful Use incentive payments from the Centers for Medicare and Medicaid Services for implementing electronic health record systems into their practices or operations are also likely aware of the fact that one of the many requirements for these incentive payments is to conduct a HIPAA security risk analysis annually.
Now more than ever, the importance of ensuring that these risk analyses are performed are being demonstrated, or providers can face dire consequences. Below are the top reasons to conduct a thorough HIPAA security risk analysis.
1. Avoid HIPAA fines and penalties. HIPAA fines can range from $100 to $50,000 per violation (or per record), with a maximum penalty of $1.5 million per year for each violation.
2. Achieve EMR Meaningful Use and receive incentive payments. If you have not performed a HIPAA security risk analysis annually, as required by the Meaningful Use program, you may have received improper Meaningful Use payments from CMS. Federal regulations require documentation be kept for six years that supports the demonstration of meaningful use as required by the incentive program.
3. Avoid potential False Claims Act Liability for improper Meaningful Use payments. False Claims Act liability can attach to providers certifying to Meaningful Use requirements without performing the mandated annual HIPAA security risk analysis. If the annual risk analysis has not been performed, the provider is not entitled to the EHR incentive payments for meaningful use. In the event a provider discovers an improper incentive payment, there are voluntary refund avenues available to diffuse the enforcement risk associated with these overpayments.
4. Protect your patients’ health information and your reputation. Your reputation as a healthcare provider is built on trust. This trust inherently assumes your patients’ sensitive health and financial information is adequately protected, and that risks and vulnerabilities that threaten that protection is meaningfully addressed. Should you have a significant breach or security incident, your patients will know about it. In part, because you are legally obligated to inform them, but it could also become headline news. Performing thorough HIPAA security risk analyses ensures that you are doing everything that you can to protect your patient’s PHI, which protects your reputation as their trusted healthcare provider.
5. Avoid investigative or litigation costs associated with non-compliance. With any enforcement action comes heightened costs, including but not limited to fines, penalties, treble damages, and even potential imprisonment. For example, under the False Claims Act, a provider could be liable for penalties up to $21,563 per claim wrongfully submitted, in addition to treble the amount received/billed to the government. As earlier noted, under HIPAA, fines can range from $100 to $50,000 per violation, with a maximum penalty of $1.5 million per year for each violation. Under certain circumstances, individuals involved in submitting the claims could personally be held liable as well. Voluntarily refunding improper incentive payments is a much cheaper avenue to take.
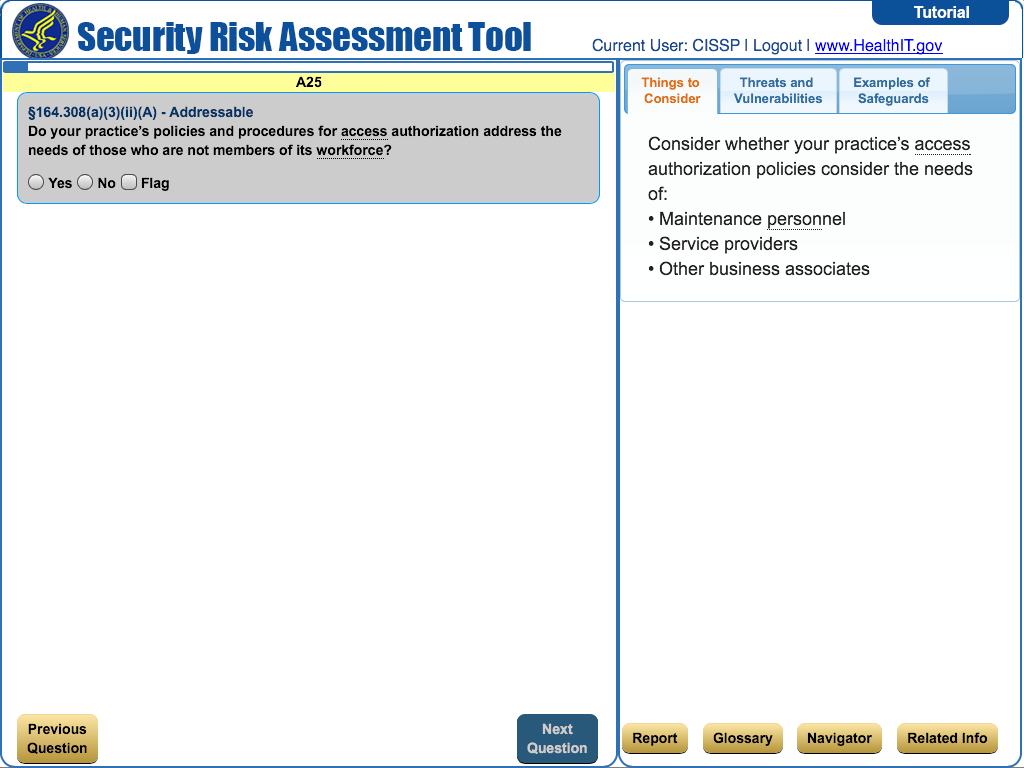
HIPAA Security Risk Assessment Tool
The HIPAA Security Rule at a Glance
There are five main areas providers need to address to meet HIPAA Security Rule requirements:
- Administrative Safeguards. All of the standards and implementation specifications found in the Administrative Safeguards section refer to administrative functions, such as policy and procedures that must be in place for management and execution of security measures. This includes the entire security management process related to the workforce, information access management, security awareness and training, contingency planning, and ensuring having business associate agreements in place with your vendors.
- Physical Safeguards. The Security Rule’s physical safeguards are the physical measures, policies, and procedures to protect electronic information systems, buildings, and computing equipment.
- Technical Safeguards. Standards and implementation specifications found in the Administrative Safeguards section refer to administrative functions, such as policy and procedures that must be in place for management and execution of security measures related to access controls, audit measures, data integrity, and data transmission.
- Organizational Requirements. Organizational requirements include the standards for business associates under contract. This standard makes it an obligation for business associates to protect PHI compliant with HIPAA, and to report violations or security incidents.
- Documentation Requirements. Documentation requirements address retention, availability, and update requirements for supporting documentation such as policies, procedures, training, and audits. Essentially this means that everything must be documented, made available to those who are impacted, and evaluated periodically for updates.
Importance of a Rigorous HIPAA Analysis
Best Practices for Security Management
- Learn about the HIPAA Security Rule
- Engage a security team
- Identify all PHI access or transmission points and staff that touch PHI
- Conduct HIPAA Security Risk Assessment
- Assign a risk level to each area
- Identify security gaps
- Prioritize gaps to address based on risk
- Create a project plan to address gaps
- Establish a budget
- Address gaps
- Engage experts to help
- Identify and train a Security Incident Response Team
- Start addressing gaps and document fixes
- Conduct ongoing security training
- Create, document, implement, and monitor adherence to policies and procedures
- Implement employee sanctions for violations
- Assign a schedule to test policies and procedures
- Monitor security adherence and systems vigilantly
- Shore up physical security
- Ensure a BAA on file with every contractor
- Consider breach insurance
HIPAA Risk Analysis Template
Conducting a HIPAA Security Risk Analysis may sound daunting at first, but it will be made easier by the understanding of the Security Rule. Once you have a full grasp of that, the next steps will be easier to implement.